Emerging Network Threats: Staying Ahead in the Cybersecurity Game

In the interconnected world, where businesses rely heavily on digital infrastructure, emerging network threats pose a significant challenge to cybersecurity. As technology evolves, so do the tactics and strategies of malicious actors seeking to exploit vulnerabilities. To stay ahead in the cybersecurity game, organizations must understand the landscape of emerging network threats and take proactive […]
Proactive vs. Reactive Security Hardening: Understanding the Key Differences

In today’s digital landscape, cybersecurity is of paramount importance. As businesses and individuals alike rely more on technology, the risks associated with cyber threats continue to grow. To combat these threats, proactive and reactive security hardening strategies have emerged as essential components of a robust cybersecurity posture. In this blog post, we will delve into […]
Network Security Assessment – A Crucial Activity

Cyber threats keep arising with sophistication and regularity, and while ensuring your network is safe is paramount, a Network Security Assessment is one of the critical steps in finding vulnerabilities in the network infrastructure. Yet a security assessment alone is not an answer to protecting your company. To protect your network effectively, a strong Network […]
Navigating the Firewall Reports Landscape: Challenges and Compliance Needs

Firewall reports are the unsung heroes of network security, providing a crucial insight into the traffic and activities on your network. These reports not only help in identifying security threats but also play a pivotal role in ensuring regulatory compliance. In this blog post, we will delve into the world of firewall reports, exploring the […]
Key Performance Metrics to Consider When Evaluating Firewall Optimization

The importance of robust network security cannot be overstated. Firewalls stand as the first line of defense against cyber threats, making their optimization a critical task for organizations of all sizes. To effectively evaluate firewall optimization, it’s essential to focus on key performance metrics that provide insights into your network’s security posture and efficiency. In […]
Maximizing Network Security with Regular Usage of a Firewall Policy Analyzer

In today’s hyperconnected world, network security is a paramount concern for businesses of all sizes. Cyber threats continue to evolve, making it essential for organizations to maintain robust security measures to protect sensitive data, customer information, and critical systems. One valuable tool that plays a crucial role in bolstering network security is the Firewall Policy […]
Firewall Rule Best Practices to Protect Your Network

The importance of cybersecurity cannot be overstated. Cyber threats are constantly evolving, and as a result, safeguarding your network and data is paramount. One of the key tools in your cybersecurity arsenal is the firewall, a barrier that stands between your network and potential threats from the internet. To maximize the effectiveness of your firewall, […]
Strengthening Your Defenses: Firewall Hardening with NSPM Solutions
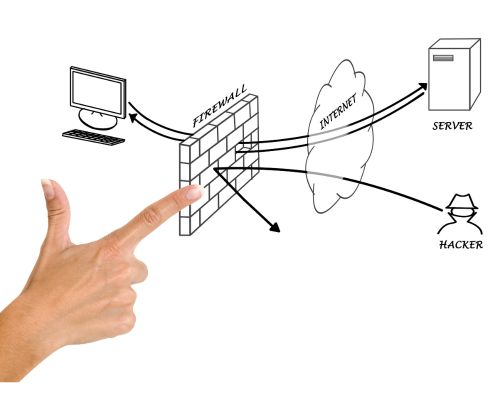
In today’s digital age, where cyber threats continue to evolve at an alarming rate, safeguarding your organization’s data and network integrity is more critical than ever. Firewalls play a pivotal role in fortifying your cyber defenses, acting as a barrier between your internal network and the outside world. However, firewalls themselves require continuous reinforcement to […]
Maximizing Network Security: Effective Usage of Firewall Policy Analysis Solutions

In the ever-evolving landscape of cybersecurity, protecting your organization’s network is paramount. Firewalls have long been a fundamental component of network security, serving as a barrier between your internal network and the outside world. However, as cyber threats become increasingly sophisticated, the effectiveness of your firewall policies is crucial. This is where analysis solutions come […]
Power of Firewall Policy Optimization: Framework Models for Enhanced Cybersecurity

In the world of cybersecurity, maintaining an airtight defense is paramount. Among the critical elements of a robust defense strategy is Firewall Policy Optimization, a process that fine-tunes your firewall rules and configurations for maximum efficiency and security. In this comprehensive guide, we’ll explore the importance of Firewall Policy Optimization and introduce you to popular […]

