Firewall Rule Analysis & Optimization with NSPM
Problem
Firewall rules can become massively complicated over time. As new applications, devices, and users are constantly provisioned and removed in networks to meet changing business demands, new rules are applied to firewalls. Also, as cybercriminals use different techniques and access paths, security teams constantly demand changes and updates on firewall policies. This intense and ever-active process can result in overpopulated rule sets. Over time, these rule sets tend to become duplicated, redundant, outdated, too generic, or non-compliant.
Rule Analysis & Optimization
Regular rule analysis and optimization are a crucial aspect of firewall management to ensure that rule sets are effective in delivering intended business and security outcomes and do not over-consume computing resources.Nevertheless, analyzing and optimizing rules can be a tedious task. Relying on spreadsheets is both labor-intensive and ineffective. Teams require an intelligent and lightweight solution to effectively address this crucial need in both small and large networks.
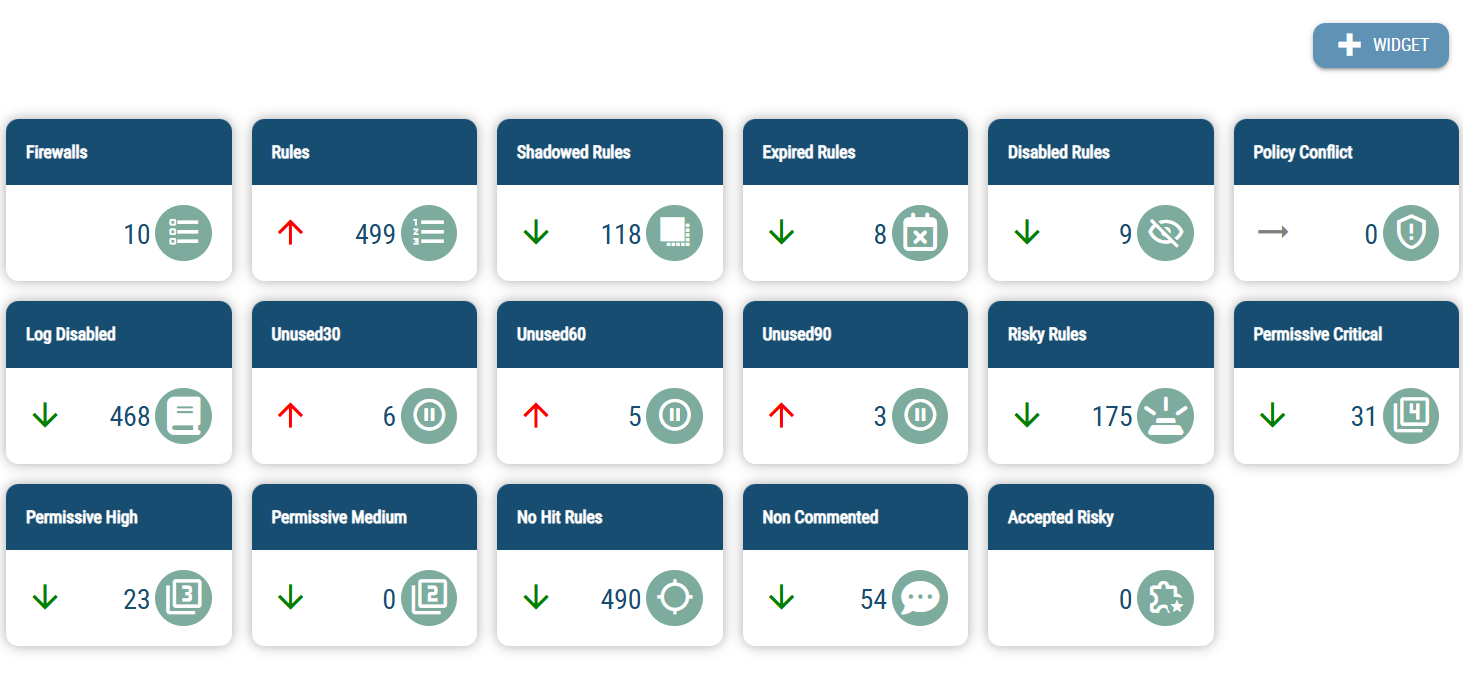
Rule Analysis & Optimization with Opinnate
The Opinnate platform enables IT teams to;
- visualize all access policies and rules across
their firewall estates – being whether on-premise, on the cloud, or both – on a single pane view - keep track of the shadowed, expired, duplicate, conflicting and permissive rules.
- apply complex queries using granular search and filtering capabilities.
- visualise network topology with the context of rules and communication paths.
- visualise objects and group objects.
- generate operational, executive level and regulatory reports.
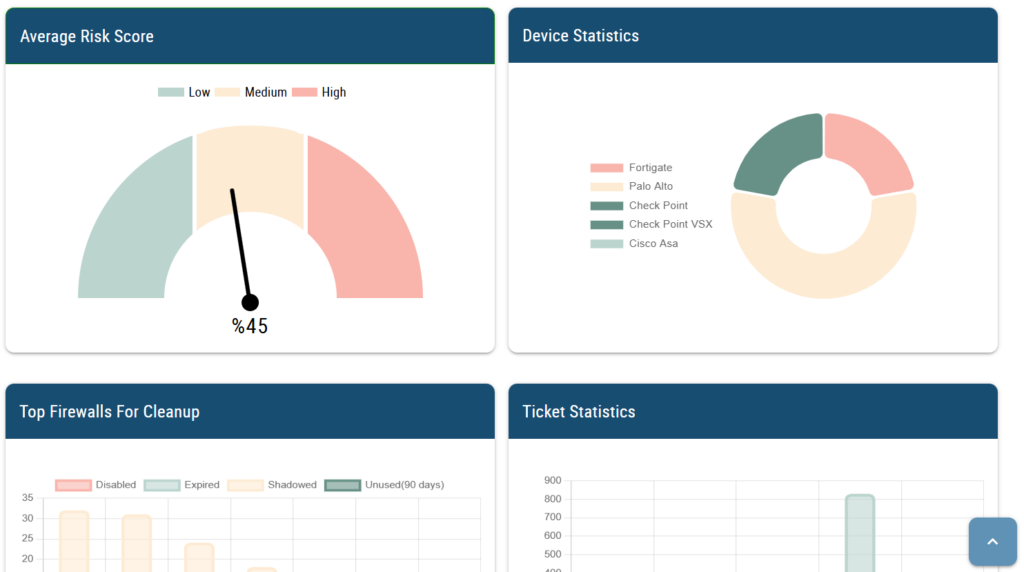


Rule Optimization with Opinnate
Opinnate greatly simplifies the optimization process. Using Opinnate,
- operation teams gain flexibility by acquiring the capability of easily taking actions on unused, shadowed, expired, and disabled rules.
- automate actions can be defined when unused, shadowed, expired, disabled are
identified. - IP addresses belonging to decommissioned servers can be quickly removed.
- reordering and consolidation get easy to implement.
- permissive rules and those involving risky services can be efficiently addressed.
- server and disk size for permissive rule optimisation is reduced up to 90%.
- the risk of human error, configuration drift, policy inconsistencies is
minimised, and version control and upgrades are simplified.
Why Opinnate?
What are the differences?
- All-in-one policy management
- No need for a management product from any firewall vendor
- More use case scenarios for real needs
- Short deployment and enablement
Why are these good for you?
- Lower TCO
- A comprehensive but simpler-to-use solution
- Less dependency to tools (Firewall management consoles, firewall analyzer)
- Less resource usage
