Navigating the Digital Landscape: Essential Computer Security Practices

In today’s interconnected world, where our lives are increasingly intertwined with the digital realm, computer security has become a paramount concern. As we rely on computers for work, communication, and entertainment, protecting our devices and data from cyber threats is crucial. Understanding the Landscape of Cyber Threats The cyber threat landscape is constantly evolving, with […]
A Comprehensive Firewall Hardening Checklist: Protect Your Network Like a Pro

In today’s digital landscape, where cybersecurity threats are continually evolving, the importance of a robust firewall cannot be overstated. Firewalls serve as the first line of defense against unauthorized access, malicious attacks, and data breaches. However, merely having a firewall in place is not enough. To ensure the highest level of security, you must follow […]
Defending Your Digital Fortress: A Comprehensive Guide to Network Security Attacks

Network security attacks have become an omnipresent threat, looming over organizations of all sizes and industries. As technology advances, so do the tactics employed by cybercriminals to infiltrate networks and compromise data. In this comprehensive guide, we will delve into the world of network security attacks, understand their various forms, and explore the strategies and […]
Unveiling the Critical Importance of Network Vulnerability Assessment

Data breaches and cyberattacks have become increasingly prevalent, safeguarding your network infrastructure is paramount. One of the essential tools in the arsenal of cybersecurity is Network Vulnerability Assessment. In this comprehensive guide, we’ll delve into the critical importance of network vulnerability assessments, how they work, and best practices to secure your digital ecosystem. Understanding Network […]
What Happened in MGM Resorts and How Could It Have Been Prevented?

Last Sunday and ironically after a couple of weeks later from Black Hat conference, MGM where this conference held, faced a cyber security attack. After this attack company market cap decreased nearly 1 B USD and since they chose to shut all systems down including web sites and slot machines lost tens of millions revenue […]
Emerging Network Threats: Staying Ahead in the Cybersecurity Game

In the interconnected world, where businesses rely heavily on digital infrastructure, emerging network threats pose a significant challenge to cybersecurity. As technology evolves, so do the tactics and strategies of malicious actors seeking to exploit vulnerabilities. To stay ahead in the cybersecurity game, organizations must understand the landscape of emerging network threats and take proactive […]
Proactive vs. Reactive Security Hardening: Understanding the Key Differences

In today’s digital landscape, cybersecurity is of paramount importance. As businesses and individuals alike rely more on technology, the risks associated with cyber threats continue to grow. To combat these threats, proactive and reactive security hardening strategies have emerged as essential components of a robust cybersecurity posture. In this blog post, we will delve into […]
Strengthening Your Defenses: Firewall Hardening with NSPM Solutions
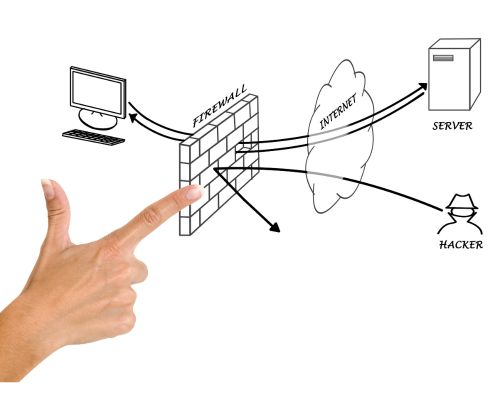
In today’s digital age, where cyber threats continue to evolve at an alarming rate, safeguarding your organization’s data and network integrity is more critical than ever. Firewalls play a pivotal role in fortifying your cyber defenses, acting as a barrier between your internal network and the outside world. However, firewalls themselves require continuous reinforcement to […]
Power of Firewall Policy Optimization: Framework Models for Enhanced Cybersecurity

In the world of cybersecurity, maintaining an airtight defense is paramount. Among the critical elements of a robust defense strategy is Firewall Policy Optimization, a process that fine-tunes your firewall rules and configurations for maximum efficiency and security. In this comprehensive guide, we’ll explore the importance of Firewall Policy Optimization and introduce you to popular […]
Guarding the Gate: Security Breaches Caused by Firewall Misconfigurations

In the relentless battle against cyber threats, firewalls stand as sentinels, safeguarding our digital fortresses. Yet, these guardians can become unwitting accomplices in security breaches when misconfigured. In this in-depth exploration, we’ll uncover the costly consequences of firewall misconfigurations and unveil strategies to fortify your digital defenses. The Firewall’s Vital Role Firewalls serve as the […]
