The Opinnate Platform
Continuous network security policy governance — with AI, risk & asset context, and governed action across hybrid environments.
Intelligence Engine
Real-time analysis
AI-Powered
Smart automation
IPAM Context
IP address management
Security & Compliance
Policy enforcement and governance
Infrastructure Control
Automated remediation actions
Network Visibility
Complete topology mapping



















“Proven in complex, regulated environments where audit readiness and change safety matter.”

90%
Connect
Seamlessly integrate with your existing infrastructure
- Firewalls + Cloud Firewalls
- SIEM / SOAR / ITSM
- IPAM Solutions
Understand
Gain deep visibility into your security posture
- Usage Analytics
- Topology Mapping
- Risk & Compliance Context
Act
Execute changes with confidence and control
- Optimize & Automate
- Governance Controls
- Comprehensive Reporting
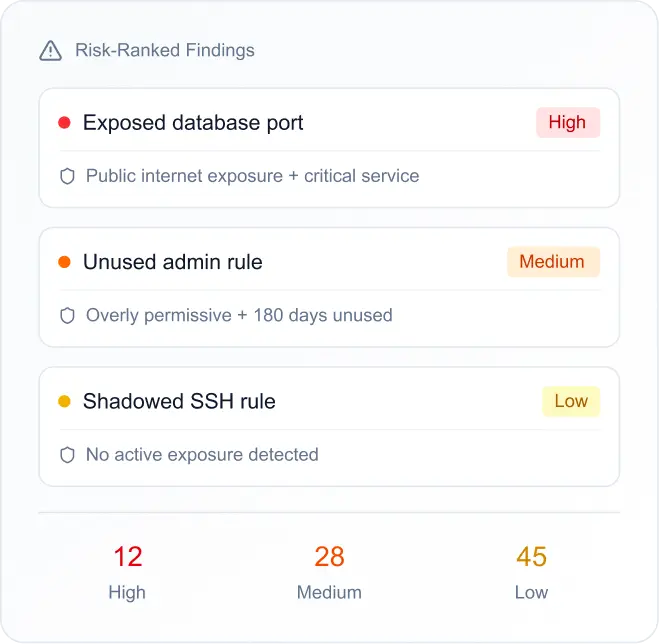
Prioritize policy issues using exposure and risk context — not just rule structure.
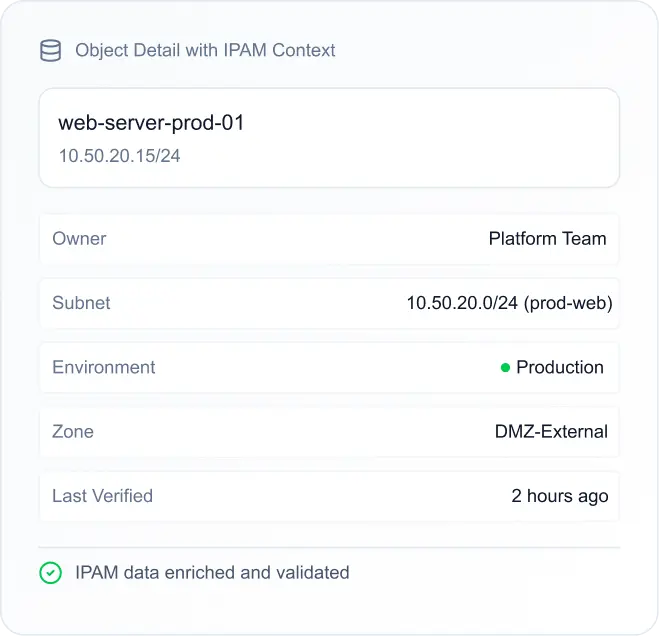
Enrich objects and analysis with authoritative IP/subnet/ownership data to reduce false positives.
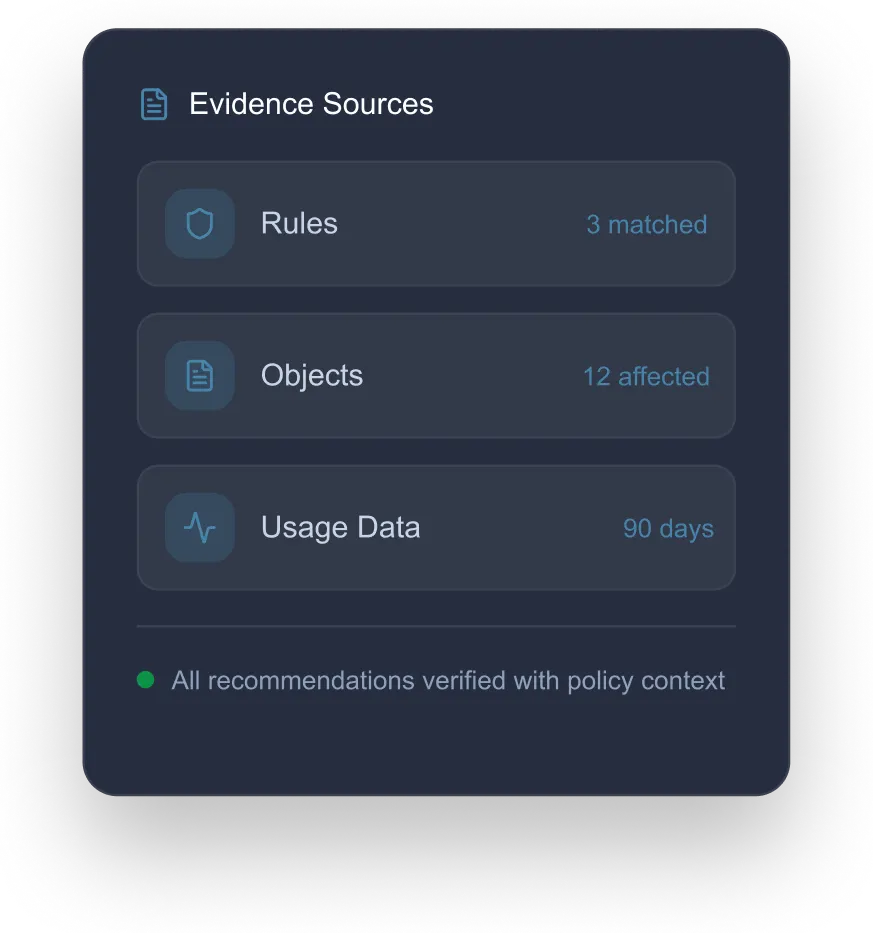
Opinnate AI is a powerful AI core delivered through Opi—an intelligent, human-friendly interface that provides clear, secure, and explainable insights backed by evidence. Whether using the chatbot, understanding policies, or ensuring AI security, Opi makes every AI output trustworthy and traceable.
Connect to on-prem and cloud firewalls, SIEM/SOAR/ITSM, and IPAM to turn insights into governed change.
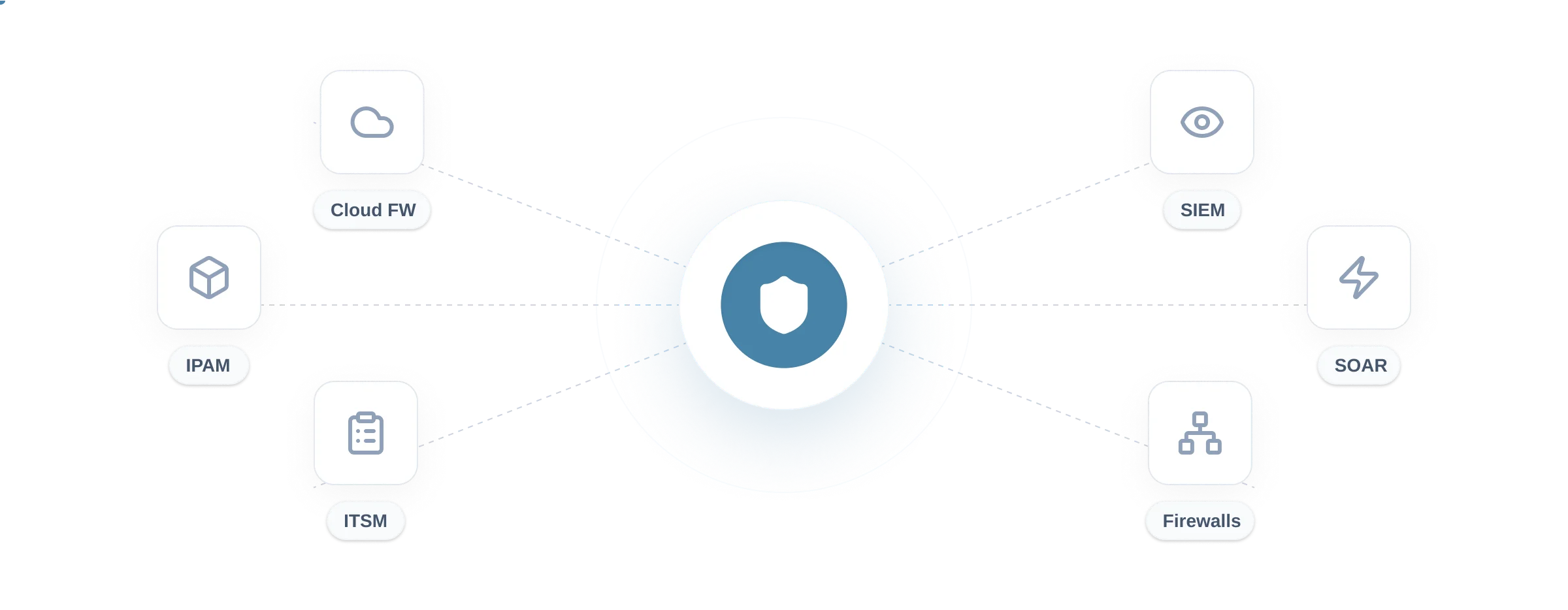







Scale your security governance from insights to full automation.
Lite
Analysis & reporting for small teams getting started with visibility.
- Policy visibility & insights
- Usage analysis (incl. passive monitoring)
- Custom reports & scheduling
- Best for: Teams starting with visibility, hygiene, and audit readiness
Standard
Optimization actions for growing organizations needing hygiene.
- Everything in Lite
- Guided cleanup actions (unused/expired, dedupe objects, consolidation)
- Scheduled optimization tasks
- Best for: Teams ready to safely reduce policy waste
Enterprise
Full automation & lifecycle governance for large scale operations.
- Everything in Standard
- Governed rule/object automation workflows
- Lifecycle management (expiring rules, periodic reviews)
- Best for: Teams scaling change volume with control and traceability
Scale your security governance from insights to full automation.
Lite
Analysis & reporting for small teams getting started with visibility.
- Shadow rule analysis
- Basic topology mapping
- 90-day history
- PDF Reports
- Email support
Standard
Optimization actions for growing organizations needing hygiene.
- Everything in Lite
- Automated rule cleanup
- Object optimization
- Scheduled maintenance
- API Access
- Priority support
Enterprise
Full automation & lifecycle governance for large scale operations.
- Everything in Standard
- Zero-touch automation
- Policy change workflows
- Custom compliance reports
- Multi-tenant support
- Dedicated success manager
App Mapping & Monitoring
License Tracking
Certificate Tracking
Firewall Backup
Switch Hardening
- Live demo on your actual environment
- Tailored to your vendors and policy volume
- Audit requirement assessment
- No commitment required




Get a personalized walkthrough
By submitting, you agree to our Privacy Policy

Head Quarters:
8, 320 Tubbenden Lane South, Bromley, BR6 7DN, United Kingdom

R&D:
Kazlıçeşme Mah. 245. SK. 5 Zeytinburnu/İstanbul Türkiye
Request your demo or get detailed information by completing this form.