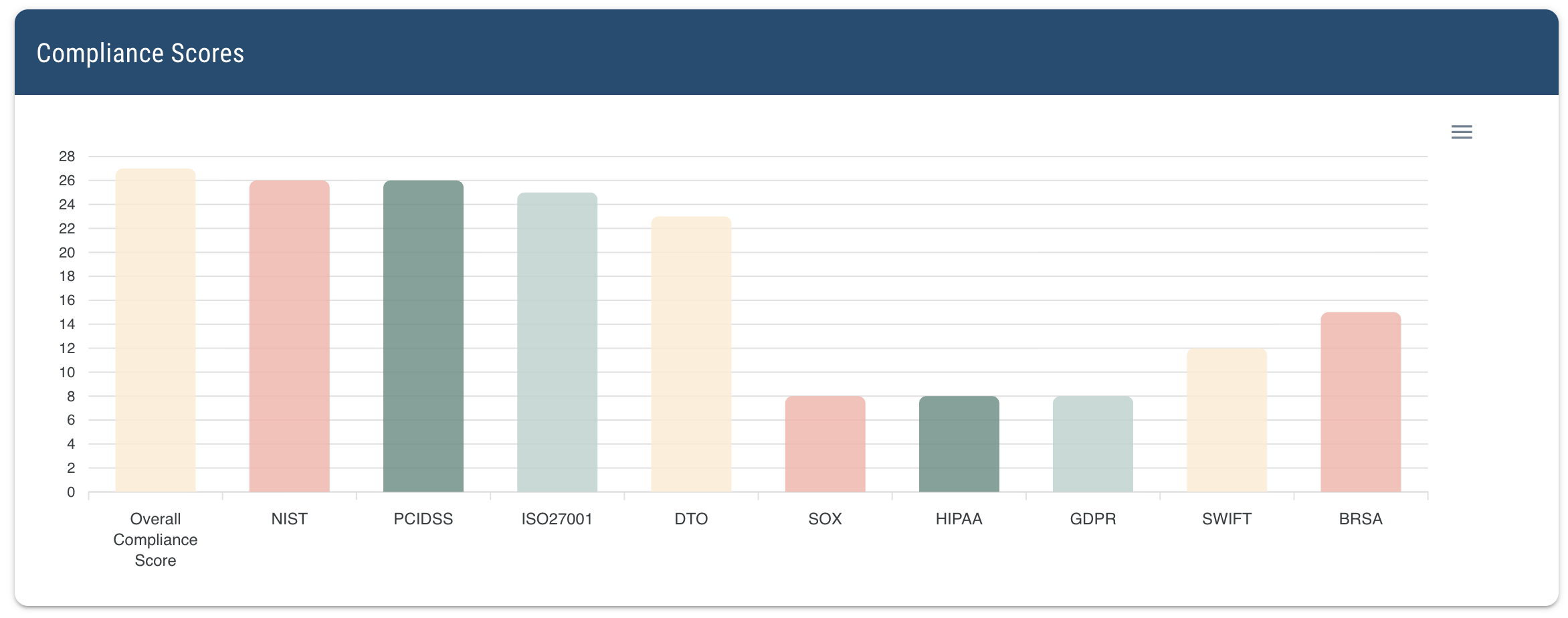
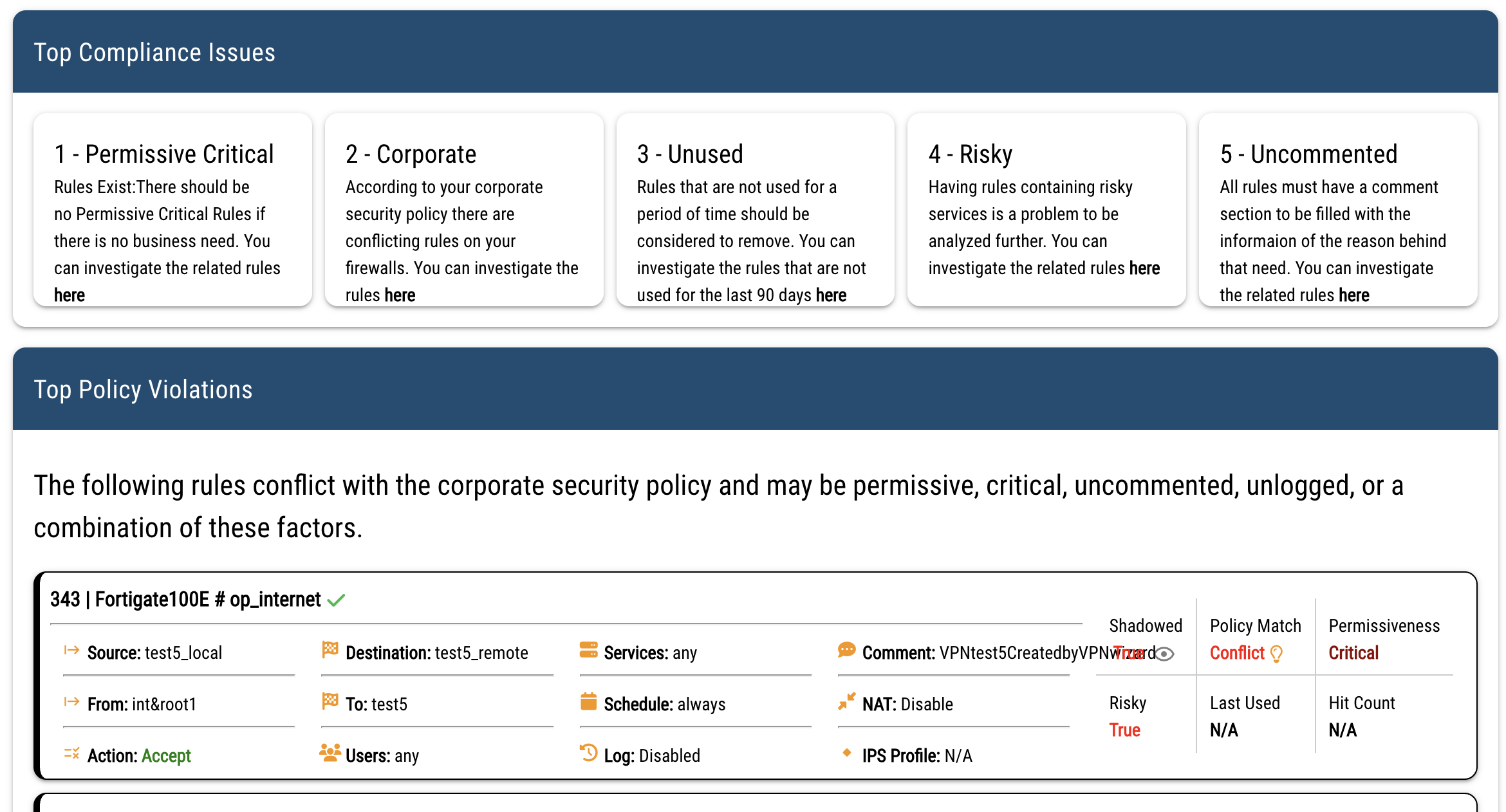
Comply with all regulations and secure your environment with best practices coming from industry standards
Following regulations and industry best practices is both a necessity for being compliant and to make all firewall infrastructure immune to security attacks
Stay audit-ready at all times with automated evidence, full change visibility, and continuous control monitoring — all in one place.
“Audit pack in hours, not days”
Problem: Audit is coming, but evidence is scattered across teams, tools, and spreadsheets.
Output: Generate an export-ready audit pack (PDF/Excel/HTML) with scheduled delivery and consistent scope.
“Prove who changed what — and why”
Problem: Auditors ask for change traceability, but firewall changes lack a clean history and ownership trail.
Output: Provide change tracking, revision history, and a clear timeline of policy changes with accountability.
“Continuous compliance, not a yearly fire drill”
Problem: Compliance checks are periodic and manual, so issues pile up until the next audit.
Output: Run recurring compliance checks and scheduled reports to surface gaps early and keep readiness continuous.
How Opinnate delivers audit-ready compliance
Opinnate turns policy data into repeatable evidence packs, with traceability and scheduling built in.
Delivery components:
Customizable templates and consistent scope for auditors.
Run recurring compliance checks and deliver reports to stakeholders.
Show who changed what, when, and how policy evolved over time.
Findings tied to rules/objects, usage signals, topology, and impact — not just static configs.

Deliverables & success criteria
Deliverables (what you receive)
A typical engagement produces a repeatable audit evidence pack and measurable improvements in traceability and readiness.
(PDF/Excel/HTML) covering agreed scope (e.g., PCI/ISO internal controls)
(who receives what, how often)
(revision history + change tracking timeline)
(top findings + recommended next actions)
(1–2 pages) suitable for audit steering / leadership updates
Success criteria (how we measure success)
A typical engagement produces a repeatable audit evidence pack and measurable improvements in traceability and readiness.
Evidence pack can be generated in minutes, not manual days
Key policy changes have clear who/what/when visibility (audit trail completeness)
Reports run on a schedule with consistent scope (no ad-hoc scramble)
High-priority gaps are identified and prioritized with context (rule/object + impact)
Security + network teams agree on scope, cadence, and ownership for audit outputs