Capabilities
Everything you need for continuous policy governance — from visibility to governed action, enhanced with AI, vulnerability, and IPAM context.
Intelligence Engine
Real-time analysis
AI-Powered
Smart automation
IPAM Context
IP address management
Security & Compliance
Policy enforcement and governance
Infrastructure Control
Automated remediation actions
Network Visibility
Complete topology mapping
Built-in context that improves accuracy and prioritization — so teams act on what matters.
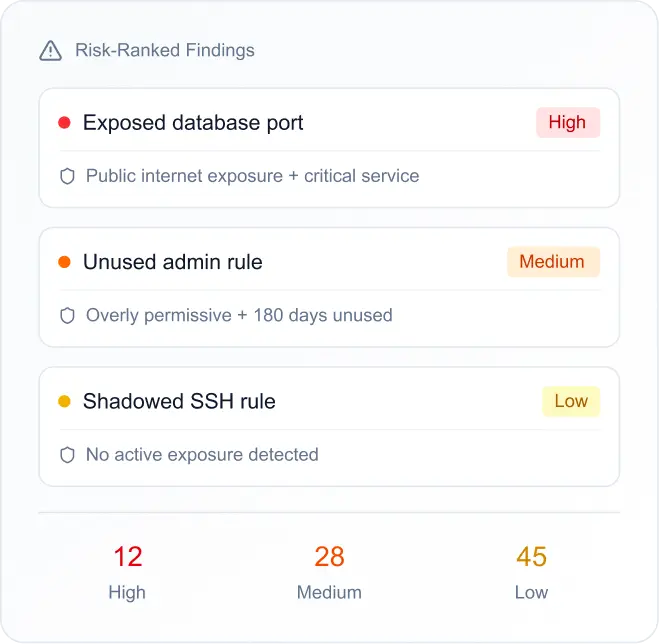
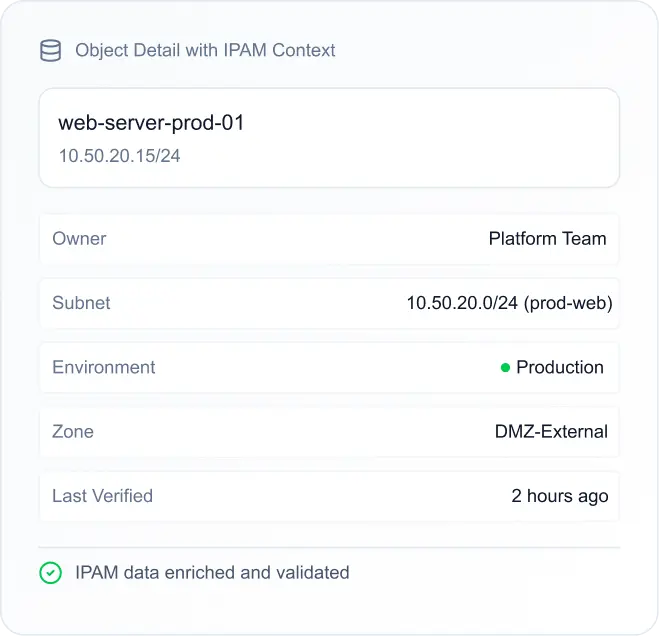
Ask questions, understand decisions, and get safe recommendations with evidence you can verify.
- "Why is this application blocked?"
- "Show unused rules in the last 90 days..."
- "Remove the old DMZ database server..."
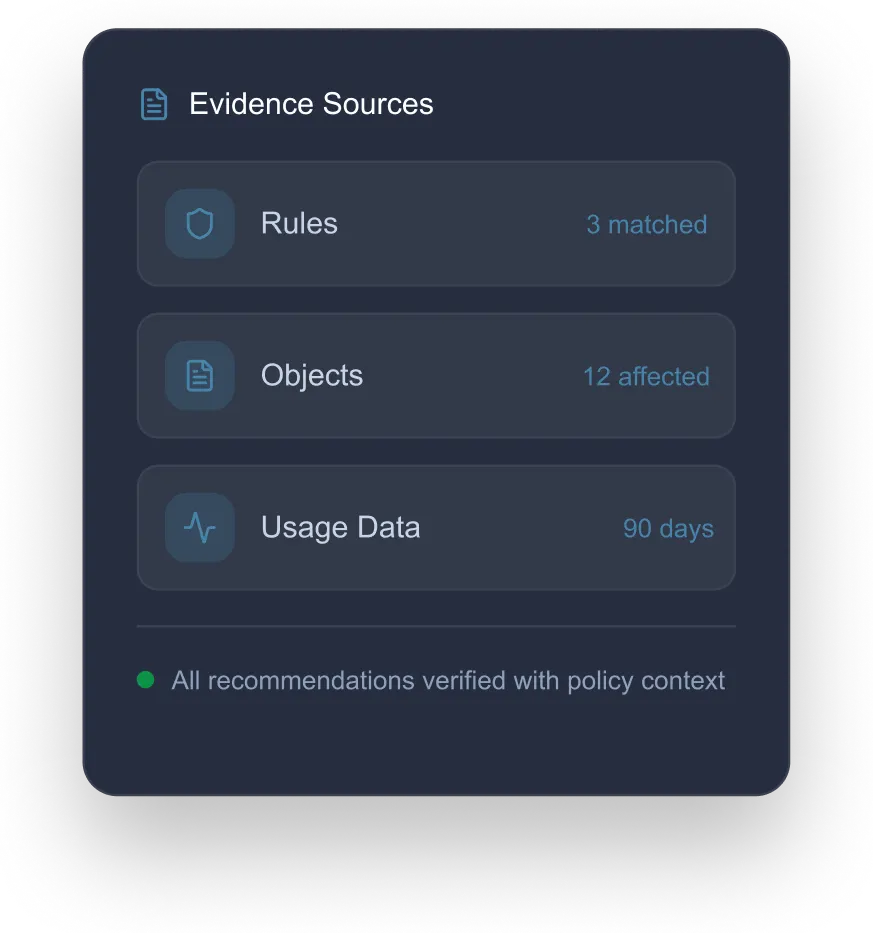
Built-in context that improves accuracy and prioritization — so teams act on what matters.
These capabilities work seamlessly across Analyze, Optimize, Automate, and Audit workflows
Scale your security governance from insights to full automation.
Lite
Analysis & reporting for small teams getting started with visibility.
- Policy visibility & insights
- Usage analysis (incl. passive monitoring)
- Custom reports & scheduling
- Best for: Teams starting with visibility, hygiene, and audit readiness
Standard
Optimization actions for growing organizations needing hygiene.
- Everything in Lite
- Guided cleanup actions (unused/expired, dedupe objects, consolidation)
- Scheduled optimization tasks
- Best for: Teams ready to safely reduce policy waste
Enterprise
Full automation & lifecycle governance for large scale operations.
- Everything in Standard
- Governed rule/object automation workflows
- Lifecycle management (expiring rules, periodic reviews)
- Best for: Teams scaling change volume with control and traceability
Built-in context that improves accuracy and prioritization — so teams act on what matters.
Lite
Visibility & reporting
Standard
Optimization actions
Enterprise
Automation & lifecycle governance
A tailored walkthrough based on your vendors, policy volume, and audit requirements.
- Live demo on your actual environment
- Tailored to your vendors and policy volume
- Audit requirement assessment
- No commitment required




Get a personalized walkthrough
By submitting, you agree to our Privacy Policy